
Cisco Asa Firewall Ios Image For Gns3 Download
Download Cisco Asa Firewall Ios Image For Gns3. ASA IOS Version 8.4 Download For GNS3 Apr 2, 2013 I have to test new Cisco ASA's IOS version 8.4 in my GNS3 LAB.
Attention, Internet Explorer User Announcement: Jive has discontinued support for Internet Explorer 7 and below. In order to provide the best platform for continued innovation, Jive no longer supports Internet Explorer 7. Jive will not function with this version of Internet Explorer. Please consider upgrading to Internet Explorer 8, 9, or 10, or trying another browser such as Firefox, Safari, or Google Chrome.
(Please remember to honor your company's IT policies before installing new software!) • • • •. The history channel salem witch trials video guide answer key.
Contents • • • • • • • • • • • • • • • • • • • Topology Downloads • • • Step 1: Extract ASA zip file. It contains the two image file ‘asa842-vmlinuz.kernel’ & ‘asa842-initrd’.
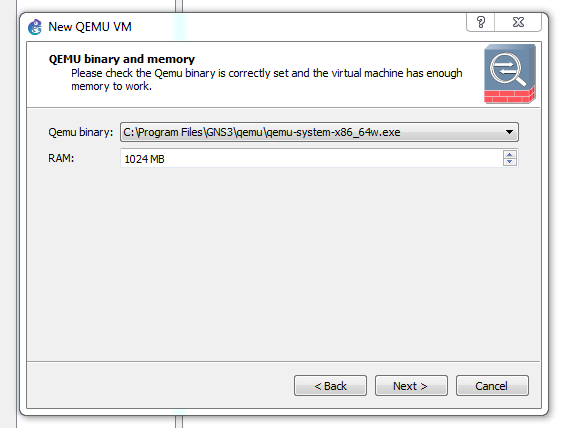
Now you need to open GNS3. Go to preferences in the edit tab.
Then go to Quemue VM. Opne a new Quemue VM by clicking new. Now set the name and type of the Quemue VM ‘ASA8.4(2)‘. Step 2: Set the Quemue Binary executable path and RAM size. Step 3: Choose initrd and kernel image into proper boot specific location. Please note that at the time of importing do not make these image as default for this platform.
Now ASA rendering to GNS is complete. Its time to explore the rest of the ASA magic. Before that please take a look of my network diagram(physical and virtual) and how I actually implemented in my virtual platform. Now to implement in my system I did the following simple steps. Please follow. • Set two Virtual network through Vmware network editor. Once you open it.
You need to power UP two Virtual Network Adapter and set their properties and attributes. Here VMnet0 is the Internal network having 192.168.0.0/24 subnet and VMnet8 is the external having 192.168.239.0/24 subnet. For both of them we need to connect a host to this Virtual adapter and VMnet0 should be host only and VMnet9 should be NAT as a property. Now all the vegetables are ready to cook. Open GNS3 and create a Network like the bottom one.
Here I took a ASA with Two cloud and two Ethernet SW. The Cloud1 and Cloud2 should be configured properly to get access of your Virtual Network card to GNS module. Now see how to configure the Cloud. Its very simple. Right click on the cloud and open settings and select proper network card and render. As the diagram says the Cloud1 should be mapped to VMnet0 and Colod2 should be mapped to VMnet8.
Cloud 1 Configuration Cloud 2 Configuration Before going to turn on the ASA I will show you a simple thing, how to share your internet connection to VMnet8(NAT Virtual Adatper). Open the Netowrk You are using to browse current Internet connection. Open properties and enable sharing the Internet over VMnet8.
See this is how you can share the Internet over VMnet8. Now Its time to launch the ASA into action Before that lets have a look at the topology once again. FireUP the ASA and open the console now. Do some besic configuration to enable the HTTP access from my inside network to launch the ASDM. Inside Configuration ciscoasa(config)# int Gi0 ciscoasa(config-if)# ip add 192.168.0.10 255.255.255.0 ciscoasa(config-if)# nameif inside INFO: Security level for 'inside' set to 100 by default.
Ciscoasa(config-if)# ciscoasa(config-if)# security-level 0 ciscoasa(config-if)# username admin password Admin.123 privilege 15 ciscoasa(config)# http server enable ciscoasa(config)# http 192.168.0.0 255.255.255.0 inside ciscoasa(config)# int gi0 ciscoasa(config-if)# no sh ciscoasa(config-if)# Outside configuration ciscoasa(config)# interface gi1 ciscoasa(config-if)# ip add 192.168.239.10 255.255.255.0 ciscoasa(config-if)# nameif outside INFO: Security level for 'outside' set to 0 by default. Ciscoasa(config-if)# security-le ciscoasa(config-if)# security-level 100 ciscoasa(config-if)# no sh ciscoasa(config-if)# Import ASDM Now we need to copy the ASDM image to ASA Flash. Before that please ensure that icmp is enable from both side and able to ping. Now turn on the TFTP server and load the ASDM on it. Ciscoasa# copy tftp: flash: Address or name of remote host []? 192.168.0.1 Source filename []? Asdm-647.bin Destination filename [asdm-647.bin]?